Patterns to secure systems end-to-end in a large enterprise

Security can mean many things depending on the context. For those who are technically inclined, security might mean investing in surveillance or firewall systems that secure physical or virtual spaces. Others might think of security as a more abstract concept – something that allows them to go about their daily life without worrying that they’ll come to harm. At its core, security is about creating the emotion of safety and removing anxiety from people’s minds. You know security is working when people aren’t thinking about security.
In the technical world, security has many implications for a large enterprise. These are only a few examples of how cybersecurity lives in an organization:
- Authentication and authorization as part of the user experience confirm whether users are who they say they are and allows a user to access specific resources. These measures protect large organizations against fraud and theft and ensure that confidentiality is maintained.
- Architecture diagrams illustrate where the security systems exist in an organization’s ecosystem, such as authentication, data protection, and information exchange.
- Who owns the enterprise’s security within the team, which in the end is a shared responsibility across many roles. Developers are responsible for handling errors and exceptions, validating using regular expression (a sequence of characters that specifies a search pattern) and writing secure code while networking teams set up systems that prevent hackers and unauthorized access.
The growing cybersecurity industry comes hand in hand with the evolving needs of large enterprises that have increasingly complex ecosystems. The global cost of cybercrime dwarfs most economies, coming only behind the GDP of the USA and China. While $3 trillion was spent on fighting cybercrime in 2015, this number is expected to grow to $10.5 trillion in 2025.
So how can your organization address security challenges in its various tools and systems? Here are our learnings from documenting and implementing security patterns end-to-end for a large enterprise:
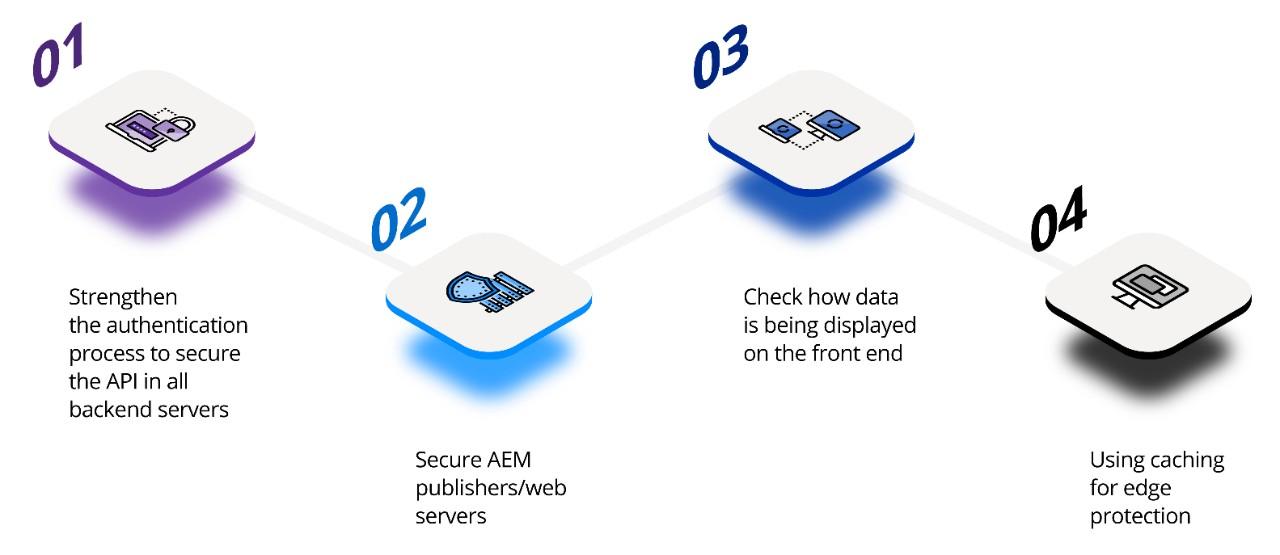
1. Strengthen the authentication process to secure the API in all backend servers
In large organizations with many APIs and data exchange points, it’s best to use user ID-based authentication and authorization rather than relying on generic IDs. The system is continually verifying who a user is before granting them the appropriate access.
2. Secure AEM publishers/web servers
This user-based access flows into front-facing applications like AEM publishers and web servers. For example, this user-based authentication and authorization can protect important information from being leaked ahead of time and spoiling months of planning for your organization in a large-scale launch event.
3. Check how data is being displayed on the front end
Even if data is being accessed securely from an API, we need to think about whether we’re storing it safely on the browser and retrieving only the data that needs to be shown to the user at that point to reduce risk.
4. Using caching for edge protection
An organization can use caching as an added security measure along with authentication and authorization – where a user can see a different view when accessing the same content.
The Netcentric Approach
This thorough process of analyzing a large ecosystem holistically and identifying all the layers and entry points made more secure is invaluable to many of our clients. Even if teams are not ready to directly make changes to their code, Netcentric can offer security as a service by creating lightweight add-ons that gently sit atop and provide full security to the existing codebase.
Netcentric’s security solutions have successfully defended against both external and internal hackers and secured the success of high-visibility, global, multi-million dollar launches in over 28 countries. We work diligently with each organization’s needs to have peace of mind doing what they do best.
Contact us today to see how we can help you secure your enterprise end-to-end.